Surviving cyberspace, lessons learned at PWN OR DIE 2024

By Paulina Collaguazo
What would you do if you lost full control of your network?
It’s eleven at night, you receive an email indicating that your Active Directory Administrator account has been revoked. How was that possible? Have you been fired? The answer is No! But someone has entered your domain and played around with the privileges. Security in Active Directory (AD) is essential to protect the IT infrastructure of any organization/company. Having excessive permissions in user groups, default credentials, uncontrolled remote access, using the same accounts for personal and administrative tasks and much more can bring serious problems and security gaps for your organization.
However, there are processes and tools that help you carry out an analysis of the security of your environment. In the event called [PWN OR DIE] have exposed tools such as [Netexec] , [PetitPotam] being quite useful in audits of security, for the Red Team and penetration tests, allowing you to evaluate the security of the environment, but additionally, if you need to do tests in a virtual laboratory [GOAD], it is an ideal pentesting project to practice common attack techniques.
Speakers didn’t only talk about Active Directory, keep reading because this will be of your interest!!
Tools such as LinPeas (for Linux), WinPeas (for Windows) were also presented in the event. Both are scripts designed to help look for insecure configurations, weak permissions, and other indicators that an attacker could exploit to escalate privileges on the system. These tools are very versatile and benefit both beginners and experts in the field of computer security.
Log management
If you are part of the computer security team, CSIRT, Blue Team of your organization, you regularly work with the famous “System Logs”. Correctly knowing the codes associated with said logs is essential, since if you come across something similar to what you can see below, what would be your interpretation and how to proceed in the face of said information?
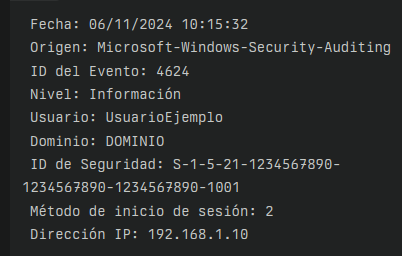
It is important to understand the log codes to identify vulnerabilities and track actions taken by people trying to access the systems. Remember: Everything you do in the system is recorded.
When you have an event like the one in the image, you can visualize valuable information. For example, the event ID (4624), can give clear information about the actions taken and the nature of the access. It’s important knowing this information and making the most of it, responding effectively to possible security incidents in your systems.
If the number of the ID was 10 it would indicate access via RDP. Managing this type of logs and other events in a more dynamic and automated way is possible with tools like [Splunk]. During the exhibition, this tool was used in a practical exercise, where we observed in real time how information on security events was obtained in an agile and rapid way in order to take quick responses to incidents and make timely decisions against computer security threats.
What other tools were exhibited?
During the two days of the event, it was also possible to learn about tools such as:
- [Wazuh], designed to simulate cyber attack environments.
- [Certipy][DWA] , can help you identify vulnerabilities in Active Directory
- Ignorant,, an interactive script that allows you to investigate which services (Instagram, Snapchat) your phone number is associated with.
- [Juice Shop], tool that can be used for safety training, CTF, etc.
- [Cyber Chief], for encryption management.
- [CAN(Controller Area Network)], etc.
As you have previously read, a wide range of applications, scripts, etc. that allow analysis in search of vulnerabilities were exhibited at the event and that is great!, but they were not the only ones.
When we do penetration testing or vulnerability analysis on the same computer where you may perform administrative and personal tasks and do not manage separate environments for the activities you carry out, you could also be affected. How can I protect myself? What other tools could I use to take care of the integrity and security of my equipment and data? . The answer is Qubes. If it is the first time you read about this tool, you will surely wonder: What is it for?
 In one of the talks, Security expert, Ola Bini, presented the tool called Qubes,. This is a security-oriented operating system, which allows you to independently virtualize each application/task in virtual machines called Qubes. You could use and configure a Qube for analysis of suspicious files or pentesting. Another Qube can be used for managing reports, personal issues, and more, so that if any of the Qubes are compromised, the damage will not spread to the rest of the virtual environments. Interesting, right?
In one of the talks, Security expert, Ola Bini, presented the tool called Qubes,. This is a security-oriented operating system, which allows you to independently virtualize each application/task in virtual machines called Qubes. You could use and configure a Qube for analysis of suspicious files or pentesting. Another Qube can be used for managing reports, personal issues, and more, so that if any of the Qubes are compromised, the damage will not spread to the rest of the virtual environments. Interesting, right?
As you may have noticed during this reading, I have talked to you about many security tools, but data privacy was also one of the pillars of this event. Cybersecurity is not only aimed at protecting the IT infrastructure of an organization or person, but also one of the most important assets, do you know what it is? Indeed, the data. In the talks speakers emphasized the importance of them. Knowing how to properly use the technology, applications and devices that we use, reading the terms and conditions gives us a clear notion of what they do with our data and the consent that we are giving about it. Yes, we must read the terms and conditions.
We should all be concerned about the privacy of our data, they are very valuable. Don’t be part of the people who say “I am not a public figure, they are not interested in my data.” Cybercriminals do not discriminate between known or unknown people, any personal information can be used maliciously. Being aware of the proper use and management of smartphones, applications, social networks, etc., will ensure that our data is not exposed and used by unscrupulous people.
Nowadays we have access to a mobile device, where we store photos, credentials, access to social networks, we use it to get around with the help of Google Maps, etc. There is a record of everything we do, so if a theft or loss of said device occurs and it is not protected with an access code/password, it will be easy to access the stored data.

Laura Zambrano, developer of the Digital Autonomy Center, gave us useful tips and tools that we can use to take care of our data. Below I will tell you a couple of them: If you use a single password to access various services (personal, work, banking, etc.), you could be an easy target, especially if your password is weak (“123456”, for example). Using a password manager can help you add an important barrier to improve the privacy of your data. If you do not have any application that helps you manage them, [KeepasXC] is an excellent recommendation for managing secure and robust keys (it is free software). [FreeOTP] is a two-factor authentication management application that improves the privacy and security of your data by adding an extra layer of protection when you log in to online services .
Final Point!
Attending these types of events is one of the effective ways to learn, share knowledge and generate networking. It is not only about listening and attending conferences or presentations, but about learning from the experiences of the speakers, creating spaces for interaction and collaboration. They are ideal spaces where learning goes beyond theory and you can learn about the latest trends, tools and innovative approaches to security and privacy. So when you can, go ahead and be part of them.
See you at the next event!