Nextcloud through Tor

This article will address the problem of data privacy in the use of file sharing services in the cloud. With free software, safe and autonomous alternatives with similar functionalities can be implemented. Under these considerations, scripts that automate the installation and configuration of your own network using Nextcloud and Tor will be available.
Introduction
The evolution of the internet has allowed more and more users to access information and communicate quickly, comfortably and nimbly. Many services have originated from the internet, for example, voice and video communication applications, online computer systems, virtual stores, etc. Not many years ago, conversations around a paradigm called Cloud Computing, or simply “the cloud”, as it is generally known, started taking place.
But what is the cloud?
Beyond commercial definitions, where we seek to get the idea that it is the group of services that are hosted on the internet to be accessed from anywhere in the world, it is generally said that the cloud is another person’s computer (companies or institutions).
And… what is the cloud for?
In the same way that you can access 24/7 to consult information or have the option to communicate, the cloud facilitates access to the services that are hosted there without the need for local teams to perform large processing tasks and having storage capacity.
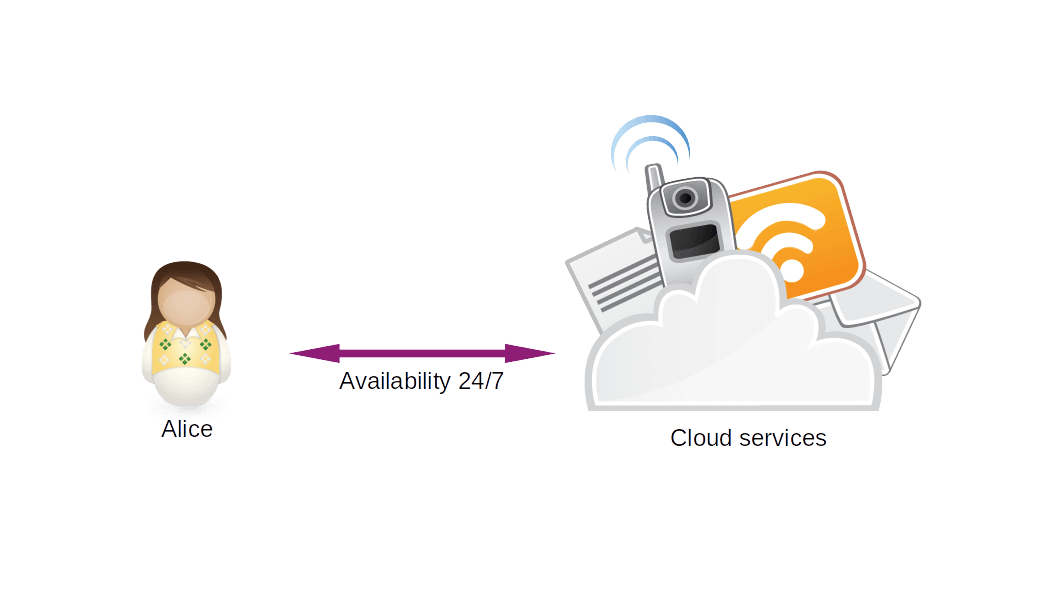 Image 1: Traditional cloud service scheme.
Image 1: Traditional cloud service scheme.
Terminology
Nextcloud: Open source code and architecture platform for file hosting and collaborative work that can be installed on a private server.
Debian: GNU / Linux distribution based on the Linux kernel, GNU tools, Debian philosophy and methodology.
Tor: is a distributed network that allows you to have anonymity on the Internet. It is commonly used through a browser that allows you to access websites anonymously. Additionally Tor allows you to expose TCP ervices accessible only within your network known as Hidden Services or Onion Services.
Terminal o consola: Environment that makes it easier for users to execute instructions on the computer through the use of specific commands.
Bash scripts: Through the use of basic programming, it allows the execution of commands in a structured manner on the command line, for among other things, the automation of repetitive tasks, managing the Operating System, etc.
Git: Software developed by Linus Torvalds for the control of changes made on files.
ISP: The entity that provides the internet service to end users, generally under a marketing model of service sales.
Disclaimer
The following article is a conceptual proposal that has not been tested sufficiently, so it is recommended to use it at your own risk.
Description of the Problem
While large cloud service providers such as Google, Amazon, Microsoft, among others, offer security and reliability in the protection of our data as part of their marketing model, it is not a guarantee that this is the case. All this due to the dark background of the already known PRISM project of the NSA, in which several Internet companies such as Facebook, Skype, Yahoo and others, delivered data of their users to US security and intelligence agencies.
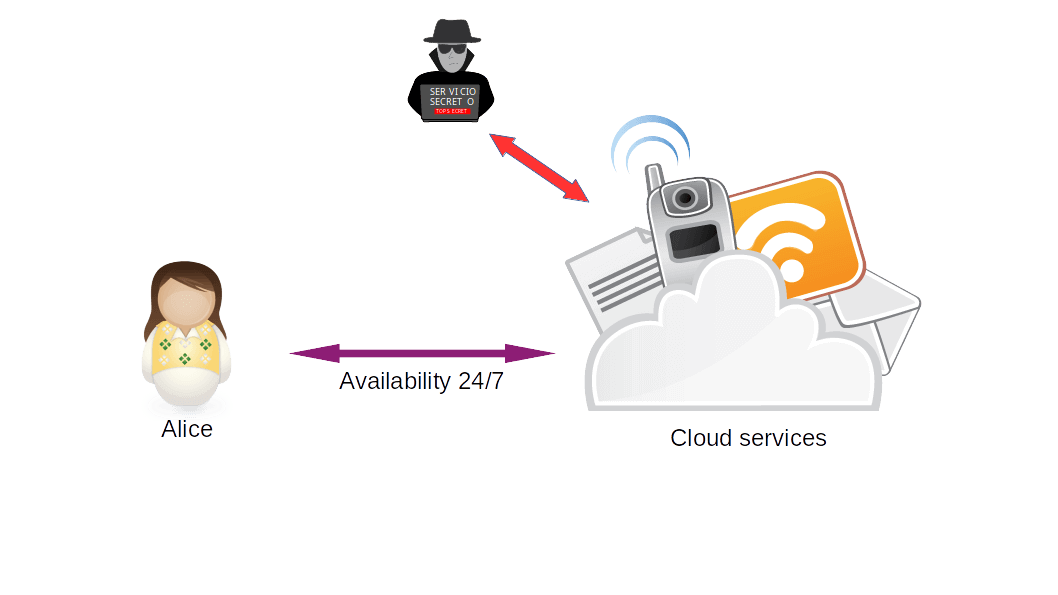 Image 2: Traditional cloud service scheme with adversary.
Image 2: Traditional cloud service scheme with adversary.
Suppose you are a user of one of the file sharing services in the cloud. For a time you worked collaboratively with sensitive information. Once this work is finished, you decide to delete this information. What guarantees do you have that the information was deleted?
In 2017, Dropbox was part of a scandal, admitted by them, in which it was recognized that files that had been deleted by users, several years ago, reappeared due to alleged system failures. This is a sign that there is no guarantee of how our data is managed by suppliers, which should affect our trust.
What to do?
Ideally, then, have our own cloud! At first glance it may seem unattainable and even impossible because you might believe that it is technically difficult and economically expensive. Fortunately, there are alternatives to most services thanks to free software, which in convergence with other technologies that seek to preserve privacy can offer a strong path to digital autonomy.
This article will provide scripts that allow the automation of the installation and configuration process of Nextcloud on Hidden Services of Tor. In this way you can have a service similar to those offered by Google Drive, OneDrive or DropBox but in a secure, private and autonomous way.
Note: “Nextcloud is a self-hosted collaboration solution……“ that offers various functionalities such as universal file access, synchronization and collaboration capabilities in desktop and web environments, video conferences, calendars, contact management, email and other productivity features.
Development of the proposed solution
Bash scripts that automate the installation and configuration of NextCloud with hidden Tor services were programmed. In this way there will be an instance of NextCloud on the local computer that can be accessed remotely by users through the use of the internet, the Tor Browser, the NextCloud Sync desktop application or the NextCloud application for smartphones, all through the Tor anonymity network without having a public IP, thus preserving user privacy and information security.
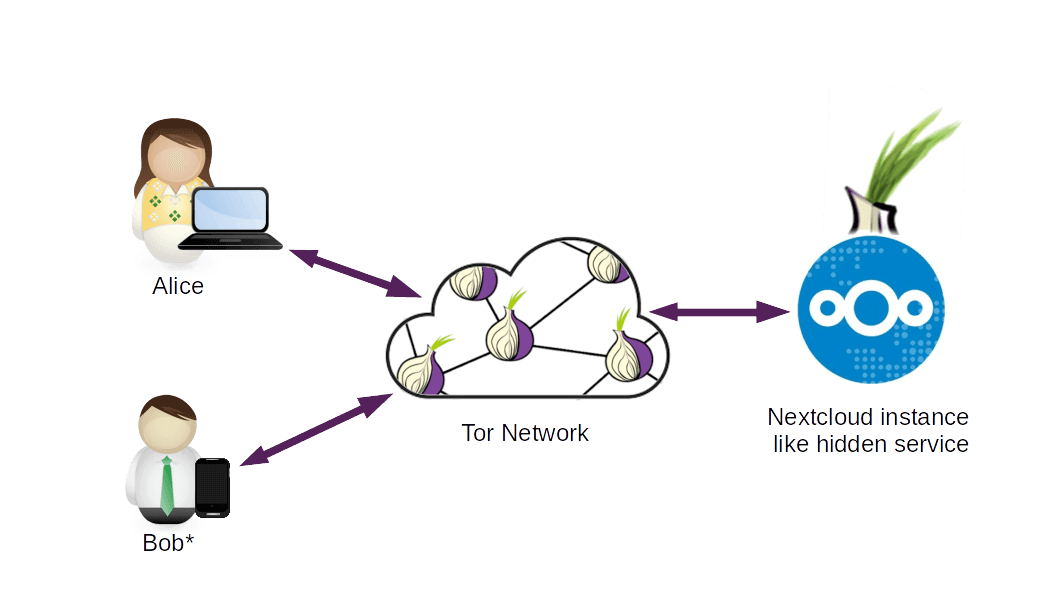 Image 3: Scheme of the proposed solution..
Image 3: Scheme of the proposed solution..
* Smart phones with Android Operating System and Orbot application.
Pre requirements
- Debian 10
- Git
- Firefox browser (optional)
- Tor Browser (optional)
Hangs on
- Open the terminal or console:
 Image 4: Open the console.
Image 4: Open the console. - Clone the repository with the bash scripts files in a local folder, by executing the following commands:
git clone https://github.com/digitalautonomy/nextcloud_onion_installer.git
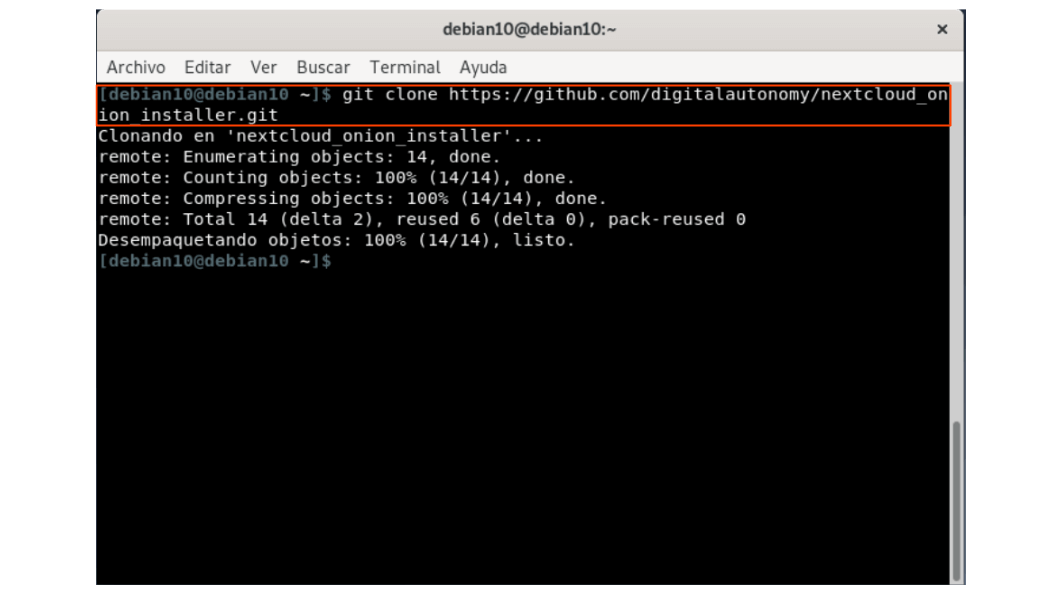 Image 5: Cloning the repository.
Image 5: Cloning the repository.
- Verify that the necessary bash scripts files have been downloaded and that they have the execution permissions:
ls -l
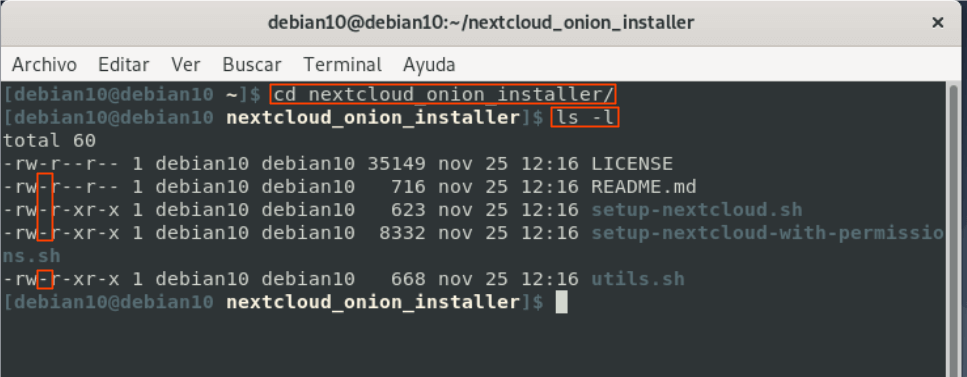 Image 6: Verifying execution permissions on downloaded scripts.
Image 6: Verifying execution permissions on downloaded scripts.
3.1. In case you do not have write permissions, add them using the command:
chmod u+x *.sh
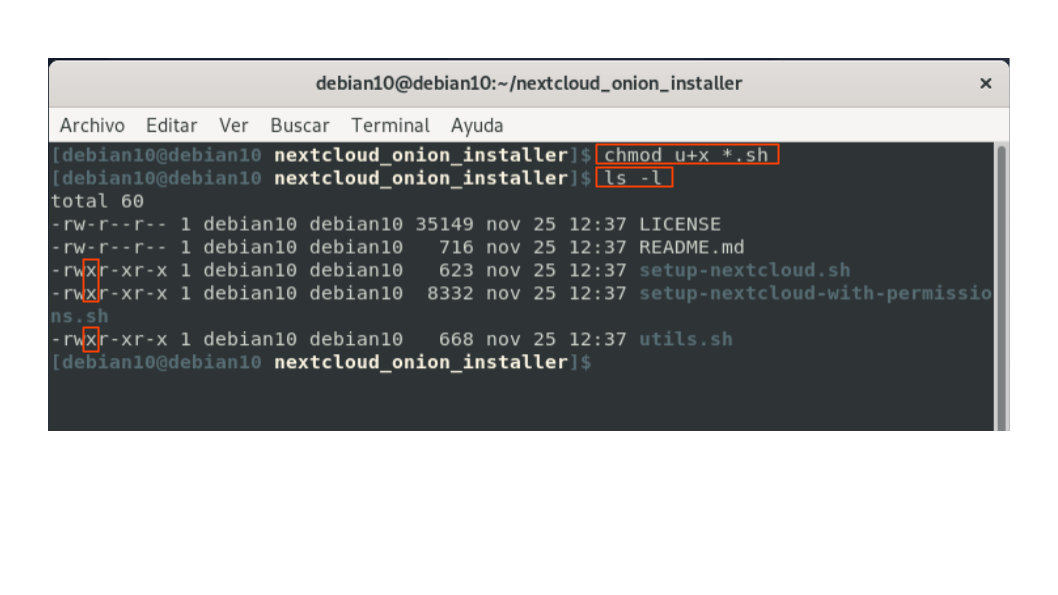 Image 7: Adding execution permissions to bash files.
Image 7: Adding execution permissions to bash files.
- Run the installer:
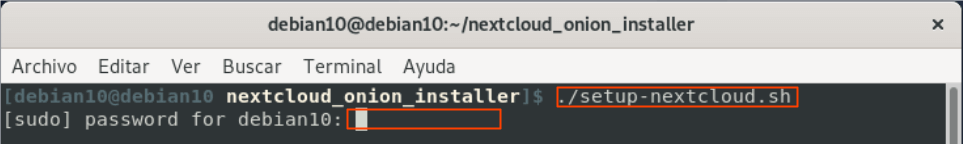 Image 8: Running the installation bash file
Image 8: Running the installation bash file
Note. Enter the required system administrator password.
4.1 Configure the credentials of the Nextcloud administrator account requested within the installation process:
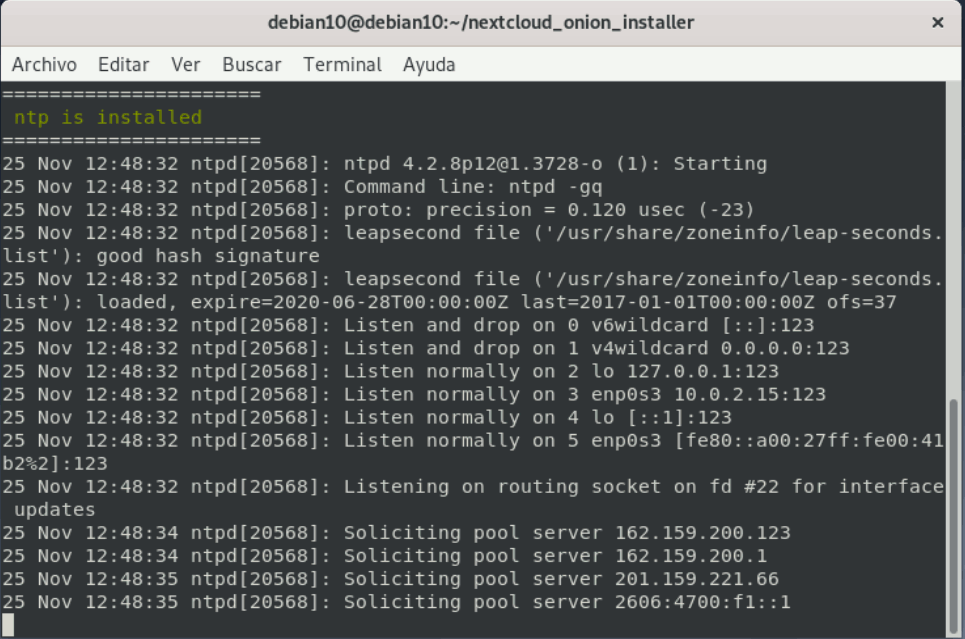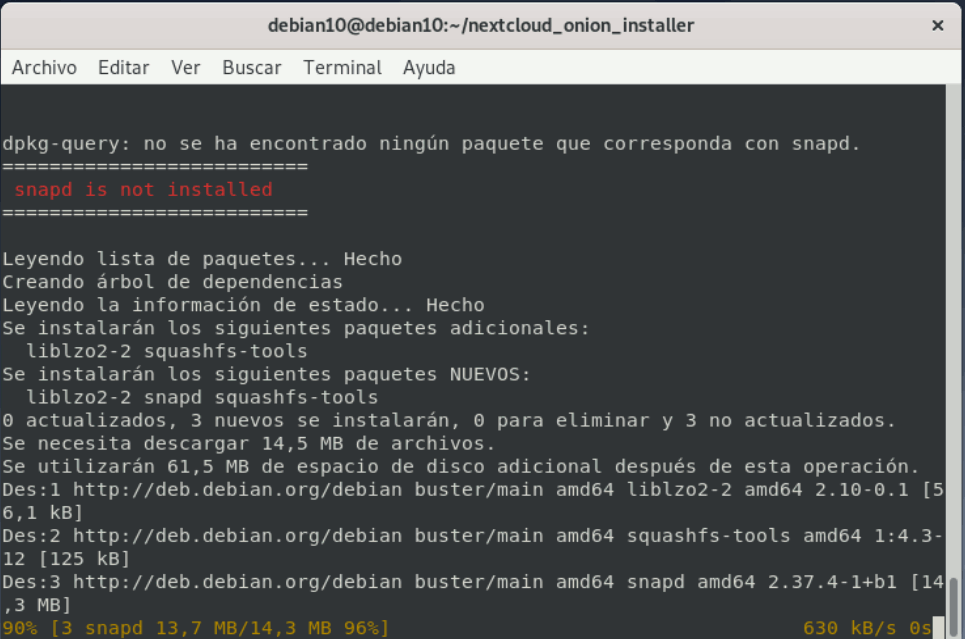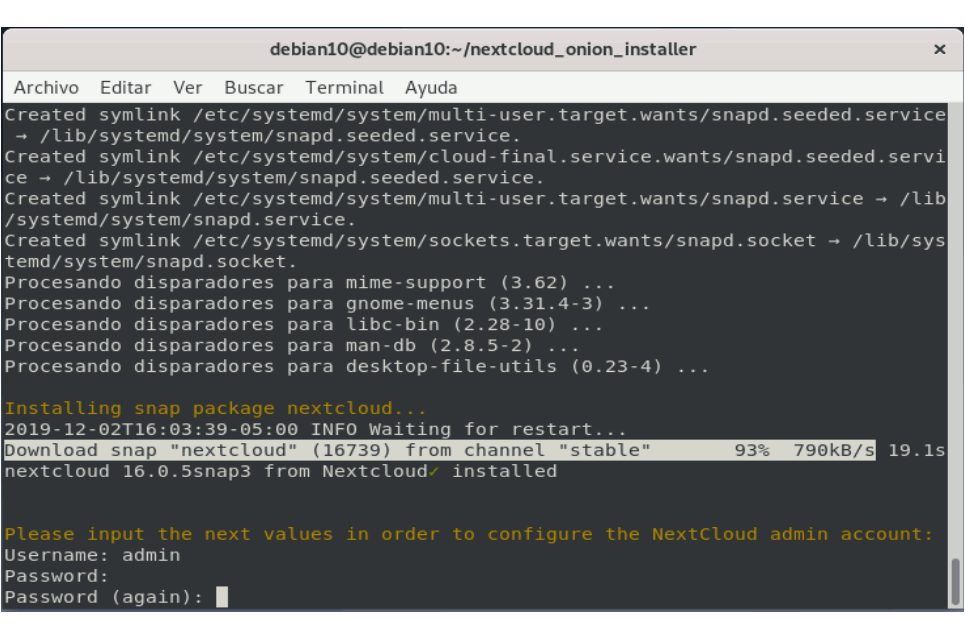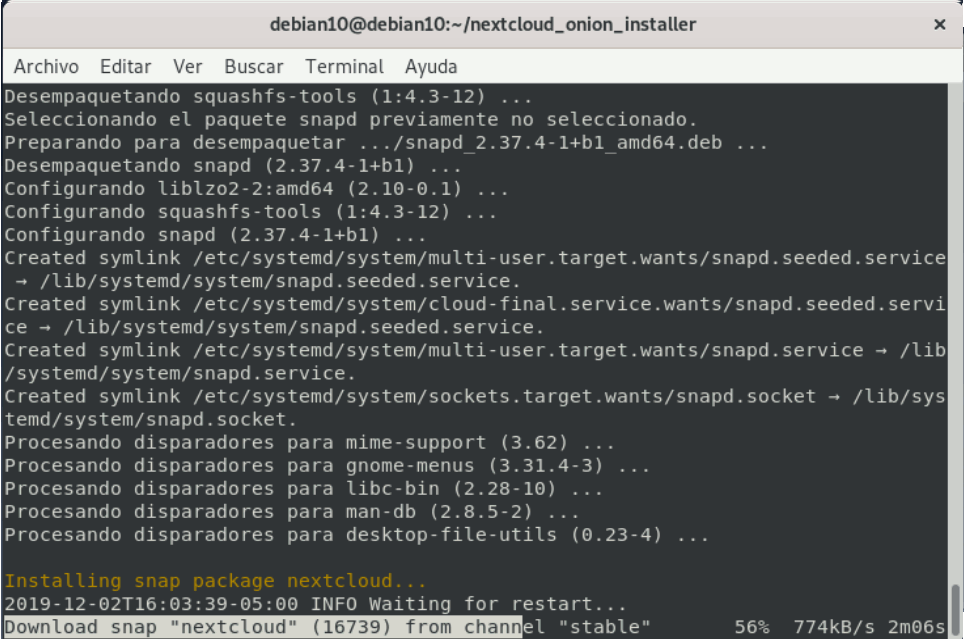 Image 9: Installation and configuration process.
Image 9: Installation and configuration process.
- (Optional) Check access to the Nextcloud administrator account with the previously configured data:
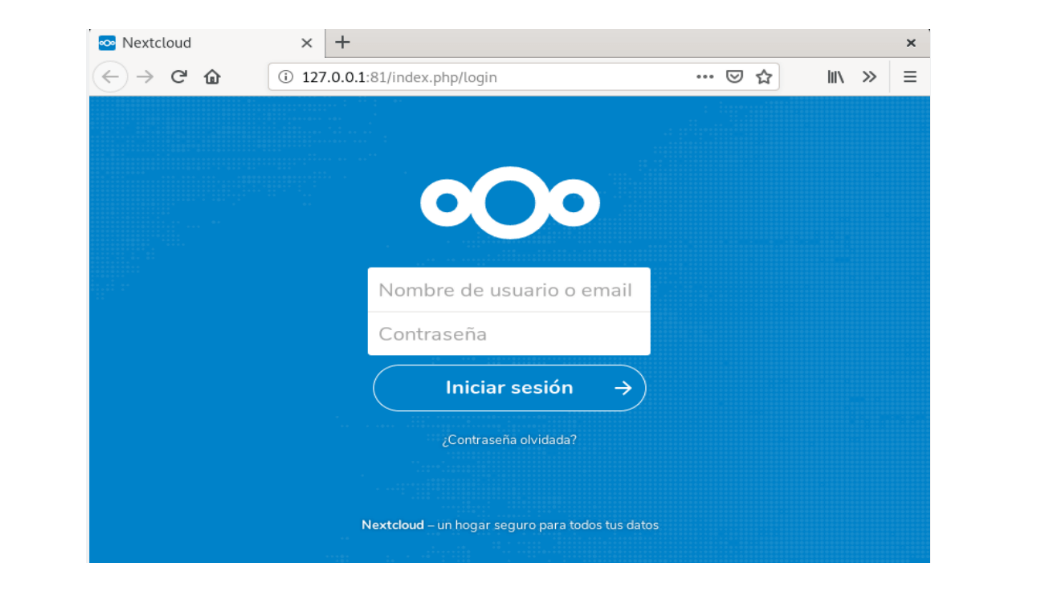 Image 10: Installation and configuration process.
Image 10: Installation and configuration process.
- (Optional) Check access from the Tor Browser to the hidden Tor service address that should have been copied to the clipboard:
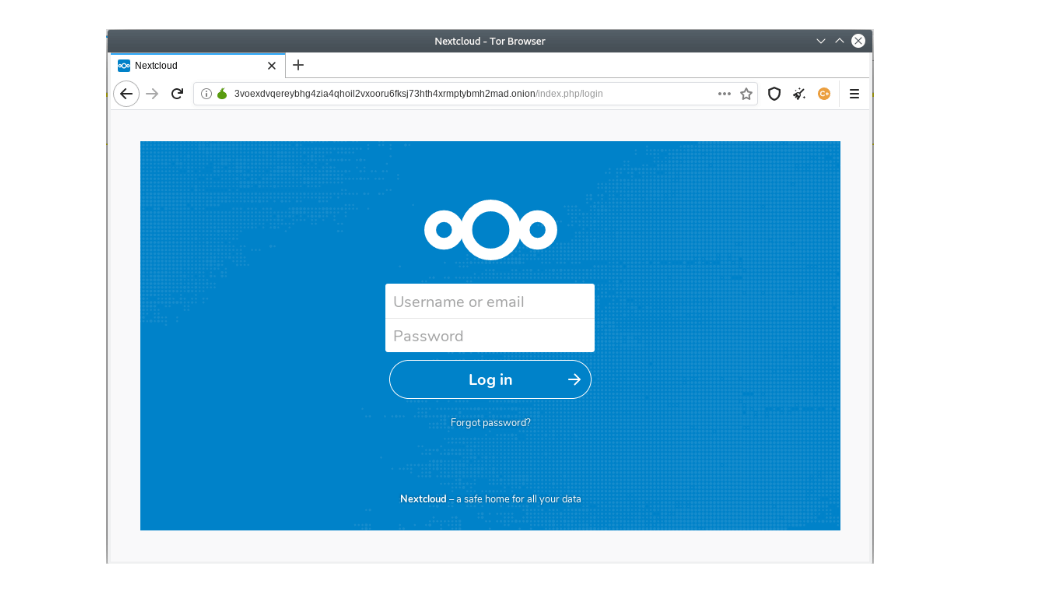 Image 11: Installation and configuration process.
Image 11: Installation and configuration process.
Conclusions
- The use of Tor’s hidden services is a very useful and powerful tool to protect privacy and anonymity on the internet. As a facilitator for the publication of services on the Tor network, hidden services allow us to make use of different platforms without relying solely on the products normally marketed on the Internet, thus providing us with a better and much more reliable alternative than those mentioned above.
- The published solution is not perfect, there are considerations to be taken into account at the time of use. Tor, by its nature, makes traffic within its network slower than the one that can occur through ISPs.
- Since there is a need to run the terminal or console, basic knowledge about its use is necessary. In future versions, we will seek to develop a tool that allows the execution of this type of solutions in a transparent way for users, regardless of the level of prior knowledge they have.
- Nextcloud is undoubtedly a great option, open source and free when it comes to having a platform that allows the exchange and storage of our documents and information, allows integration with third-party applications to provide greater robustness to their own functionalities . It is an autonomous and secure proposal to platforms such as Google Drive, Google Docs, DropBox, OneDrive, Office 360, Skype, etc.
Source code
The source code can be downloaded from the repository: https://github.com/digitalautonomy/nextcloud_onion_installer.git