Two-Factor Authentication

In the previous article we reviewed some important concepts around password handling and how to generate them in a more secure way.
In the previous article, we reviewed some important concepts around password handling and how to generate them in a more secure way. This could be the first security door in any system. Assuming you have a key for each door in a building, each one is used at its corresponding door and it opens without difficulty. But, if someone takes one of the keys or make a copy, knowing which door to open with that key, the security of the door and of the entire building is compromised.
When a password is used for each account that is managed, security is improved, but this is still insufficient for cases where passwords are compromised by one of the many causes of data leaks. Users frequently are victims of phishing attacks, being this type of crime, one of the most common and an effective way that allows 3rd parties with bad intentions or criminals, be made of private or confidential information in a fraudulent way, using emails, messages or even phone calls. One of the most common cases, is when you receive an apparently genuine email, with a link to a login page similar to Facebook, Google, or Instagram, in which inserting your username and password, allows the attacker to capture the information provided, which would grant him/her access to any of the websites mentioned previously.
However, using the same example mentioned above, the situation improves if the attacker with a key, tries to open the door and finds another one that requires a different key than the one used before. This is known as Two-Factor Verification.
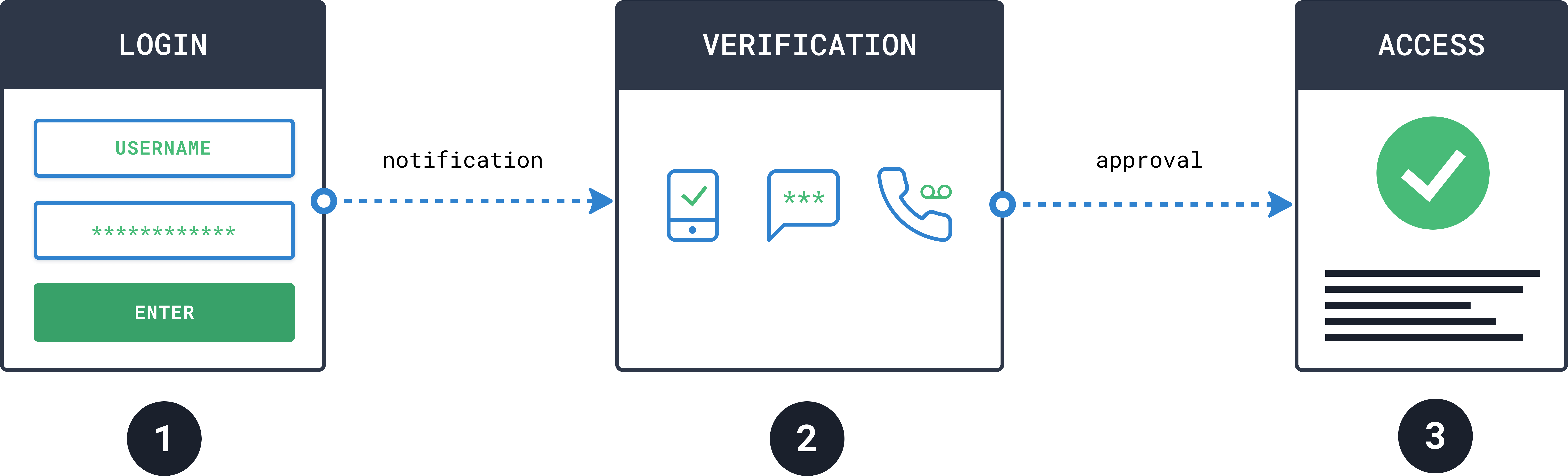
Two-Factor Authentication
Two-Factor Authentication (2FA) is a method to confirm that users are who they say they are, combining two or more of the following factors:
- Something the user knows (eg. a password, the answer to a question)
- Something that the user has (eg. a phone, a coordinate card)
- A physical characteristic (eg. biometric data, voice, fingerprints)
A real example of this type of verification is when you withdraw money from an ATM. The machine requests to insert the debit or credit card (something that is owned) and a secret code known as PIN (something that is known). When using these two components, the ATM validates the identity and allows the withdrawal of the requested money.
Something you know
This factor is basically what the user knows, for example a PIN or password. The levels of security in this type of factor, varies according to the systems that implement it. Some, for example, ask for a 4-digit code, but others use an answer to a security question, the latter variant being one of the most insecure, because the answers can be determined by having information about the person’s life as a date of birth, name of a pet, number of children, etc., and it does not take much effort to achieve it.
Something you have
This factor involves an object, normally delivered by the person or organization that performs the identity verification. Some banks, for example, when you want to make a transfer or some operation that requires an identification of the user’s identity, request a random code that is usually obtained using a coordinate card, which is nothing more than an array of letters (usually from A to F) and numbers (0-9). To do this, the system requests a combination that can only be obtained according to that card.
This, combined with the “something you know” factor, is one of the most popular. The formula consists of:
SOMETHING THAT IS KNOWN + SOMETHING THAT IS OWNED.
User physical characteristics
The companies that sell computers and smartphones implement this type of identification in their products, with the intention of making it easier for the user to unlock their devices. For example, today a smartphone can be unlocked using fingerprints, some biometric feature (facial recognition) and the voice itself.
Using physical features as an authentication factor, seems a safer method for users of these devices, but that also implies a risk. Since a password or code can always be changed, but not the physical characteristics. To unlock a device using these features, contrary to the will of the owner, there are multiple methods available to do so. In this regard, Hollywood has given enough ideas on how to achieve it with James Bond-style or Mission Impossible movies.
One-time passwords
So far it has been described what are the types of components of a Two-Factor authentication, but which ione is the most recommended? The answer to this question depends on the threat model you are facing and how they can be used in correspondence with each threat model. In this case, for a common user, a good option would be the use of passwords that are used only once time. Passwords used once or one-time password (OTP), as the name implies, are passwords or types of passwords that are valid for a single session. This type of passwords, has a superior advantage over traditional passwords, like avoiding attacks of the repetition type. Some systems that use one-time passwords ensure a 2FA implementation, requiring the user to have access to something they own (such as a phone) or something the person knows.
Among the types of single-use passwords, there are two popular ones, the HMAC-based One-time Password (HOTP) and the Time-based One-time Password (TOTP). The main difference between the two types is that HOTP generates valid passwords until a second HOTP is used or generated. In the second case, with TOTP valid single-use passwords are generated for a time limit, that is, if the time for which the password is valid expires, then that password ceases to be valid and then is discarded . Some popular companies implement 2FA services using both HOTP and TOTP services.
TOTP, while still an extension of HOTP, has security improvements with respect to these. They have been adopted as a standard by the Internet Engineering Task Force. Although they are safer, among other causes, they are vulnerable to certain types of attacks in which credentials can be captured just like traditional passwords.
Case study
Since TOTP is a recommended method, the following exercise will configure this factor in a specific scenario. To do this, a Two-Factor authentication application is required to be installed on the phone for systems that use single-use password protocols. In this case, FreeOTP, an Android and iPhone app that implements the HOTP and TOTP standards, will be used.
Enabling TOTP on GitHub
Once the login to GitHub is complete:
1. In the upper right corner (navigation bar), click on the profile picture and then click on the “Settings” option
2. In the user settings sidebar, click on “Security”
3. Under Two-Factor authentication, click on “Enable Two-Factor authentication”
4. On the Two-Factor authentication page, click on “Configure using an app”
5. Save the recovery codes in a safe place
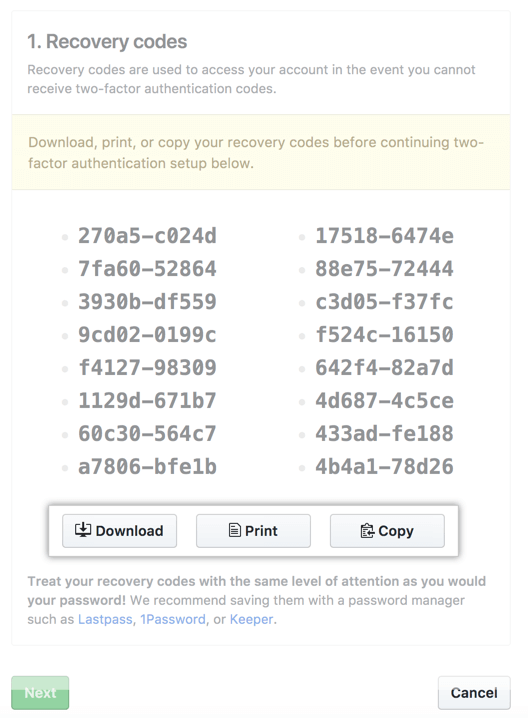
Recovery codes allow you to recover access to the account if you lose access.
6. After saving the Two-Factor recovery codes, click on “Next”
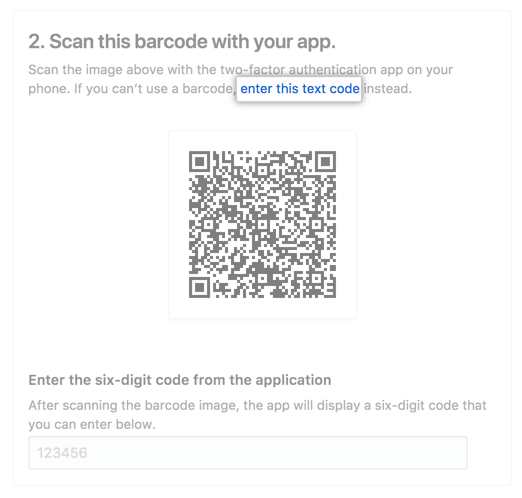
7. On the Two-Factor authentication page, perform one of the following options
- Scan the QR code with the mobile device app. After scanning, the app shows a six-digit code that must be entered in GitHub.
- If the QR code cannot be scanned, click on “Enter this text code” to see a code that can be copied and manually entered into GitHub.
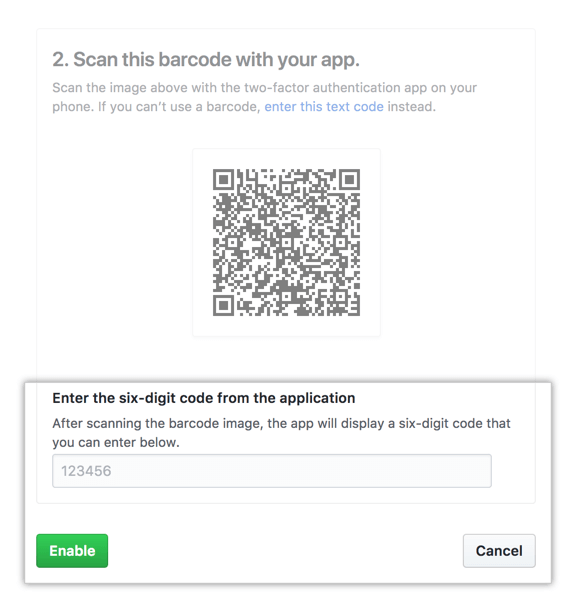
8. The TOTP mobile application saves the account on GitHub and generates a new authentication code every limited time
In GitHub, on page 2FA, write the code and click on “Enable”.
More information is available at GitHub
Resources and tools
TOTP cloud-based applications:
- 1Password
- Authy
- LastPass Authenticator
- FreeOTP
- Search results for Two-Factor authentications apps
Enable 2FA on popular sites:
Conclusions
Verification in two or multiple steps does not guarantee the security or integrity of the information of a user in a whole system, some of them are not enough, but they greatly improve it by performing the most complex process and adding extra steps to User identity confirmation. The use of password managers helps to have secure and different passwords for each account, but this method is not enough to defend against phishing. The use of the 2FA is an effective way to defend against such attacks.
References
- https://en.wikipedia.org/wiki/Multi-factor_authentication
- https://www.welivesecurity.com/2014/02/11/Two-Factor-authentication-what-is-it-and-why-do-i-need-it/
- https://en.wikipedia.org/wiki/One-time_password
- https://en.wikipedia.org/wiki/HMAC-based_One-time_Password_algorithm
- https://en.wikipedia.org/wiki/Time-based_One-time_Password_algorithm