Mumble and Tails

In a digital world, internet calls have become an alternative for global communications at low cost; they are used daily by millions of people.
- Introduction
- Terminology
- Disclaimer
- Problem Description
- Proposed Solution
- Hands On
- Conclusions
- Source Code
Introduction
In a digital world, internet calls have become an alternative for global communications at low cost; they are used daily by millions of people. While the benefits of this technology are obvious, the implications related to privacy are unknown by most users. So, it is worth asking if someone could monitor, record or listen to these calls.
The threat model and the proposed solution for it will be explained in the first section. The traditional communication model versus an autonomous one is schematized through images. The use of the proposed solution is explained in a practical way in the second section of the article. Finally, the conclusions and recommendations are presented at the end.
Terminology
Mumble : A client-server system that allows audio communications between two or more people through the Internet.
Tails: A live operating system aimed at preserving privacy and anonymity based on Linux and Tor. If you do not know how to install it, it is recommended to follow the official documentation.
Tor: Tor is a distributed network that allows anonymity on the Internet. It is commonly used through their browser, which allows you to access websites anonymously. Additionally, Tor allows exposing TCP services that are accessible only within the Tor network known as Hidden Services or Onion Services.
VoIP: Voice over IP (VoIP) communication allows establishing voice calls through data networks, the most common use is through the Internet.
Disclaimer
The following article is a conceptual proposal that has not been sufficiently tested yet, so it is recommended to use it at your own risk.
Problem Description
IP telephony services such as Skype, Hangouts, WhatsApp and others allow quick and cheap communications globally. While the benefits thereof are evident; there are also implications related to privacy. The aforementioned centralize the communications of billions of people. For example, Microsoft, in the case of Skype, or Google, in that of Hangouts, have full access to all communications that cross their servers, as can be seen in Image 1.
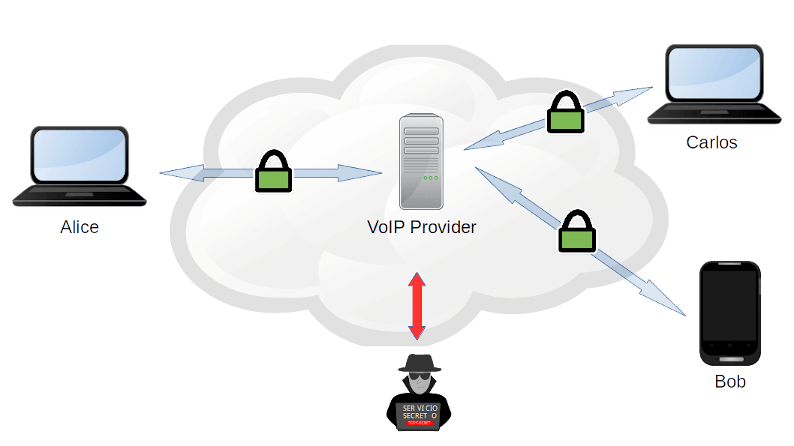
Image 1: Traditional VOIP scheme.
For this reason, if the communication is not end-to-end encrypted, these companies can spy on their users’ calls. If they were encrypted, providers would not be able to listen to the communications but would have access to their metadata. Which would allow them to know who communicates with whom, how long the call lasts, the members involved, their geolocation, their IP address, and so on.
The solution proposed in this article seeks to allow two or more people to communicate avoiding the risks stated above. For example, the communication would be carried out without anyone else knowing that it existed. To achieve this goal, the combination of Mumble systems and Tails will be used.
Tails is an operating system based on Linux and Tor that, among other things, allows instant messaging and encrypted mail. These technologies combined with the Tor anonymity network allow to hide the data and metadata of the communications; however, Tails does not provide the ability to have secret voice communications. Unlike text, voice ones usually work using the UDP protocol that is not compatible with Tor.
Mumble is an audio conference system used as a complement for online video games and meetings over the Internet. It has the feature of using low bandwidth and working well with low latency connections. In addition Mumble, unlike other VoIP solutions, is compatible with the TCP protocol, so it can work with Tor.
Proposed Solution
Bash scripts were developed to automate the installation of Mumble in Tails, both in persistent mode and in amnesia. These scripts also configure a Tor hidden service for the Mumble server. The name of the hidden service serves as the address to which the conversation participants will have to connect. As one of the participants will run the Mumble server, no one outside the conversation will know that the communication occurred, as can be seen in Image 2.
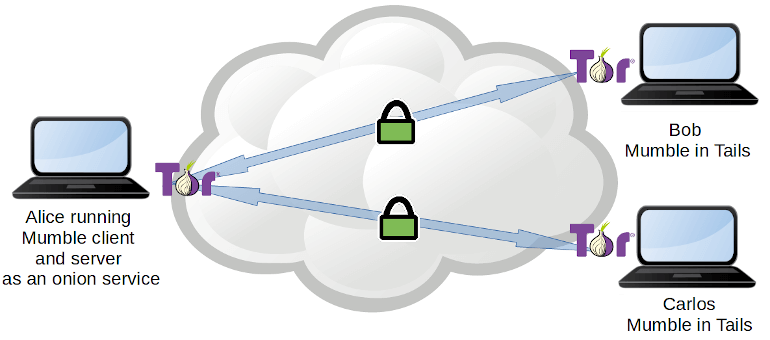
Image 2. Solution Mumble with Tails.
The scripts are described below:
setup-mumble.sh
- Update the apt repository.
- Install Mumble client and server.
- Configure the Hidden Service.
- Show in screen the Hidden Service address and copies it to the clipboard.
In persistence mode, copy all configurations of the Mumble server and the Hidden Service to the persistence folder.
purge-mumble.sh
- Removes the Mumble and Hidden Service configuration.
- Eliminates the packages for the mumble-server, mumble, and the dependencies that are not needed anymore.
restore-mumble.sh
- To be used only in persistence mode.
- Copies the configuration for Mumble and Hidden Service from the persistence volume to the respective location expected by these services.
- Restarts Tor to expose Mumble trough the Hidden Service.
- Shows in screen the Hidden Service address and copies it to the clipboard.
Hands On
Boot Tails operating system and in the welcome screen configure a root password.
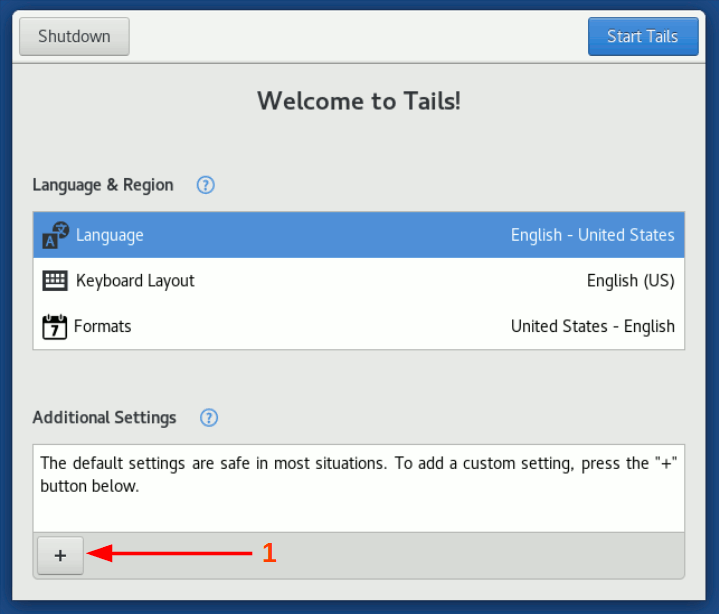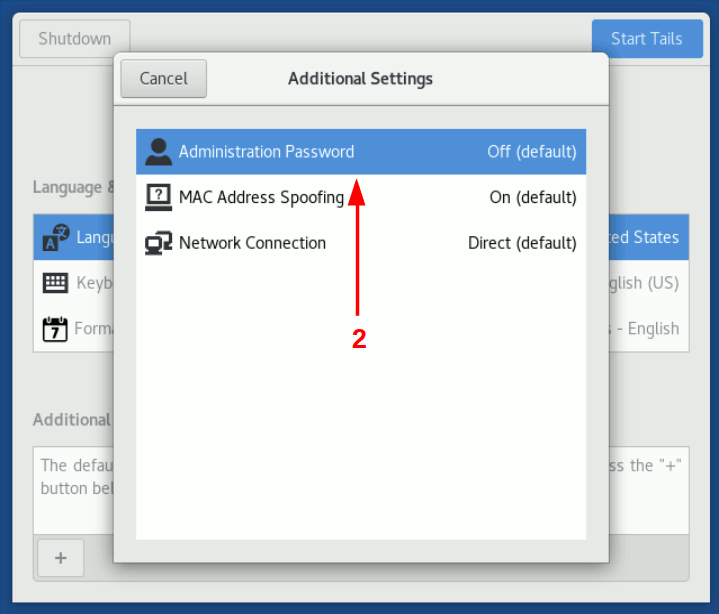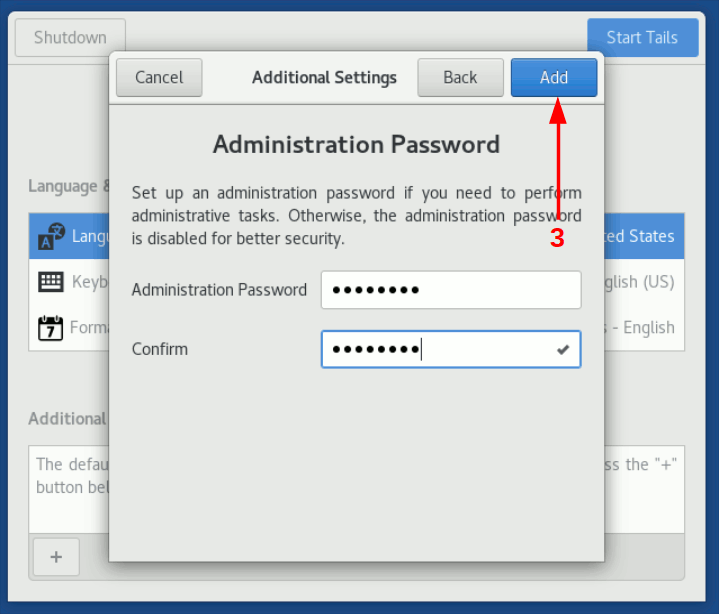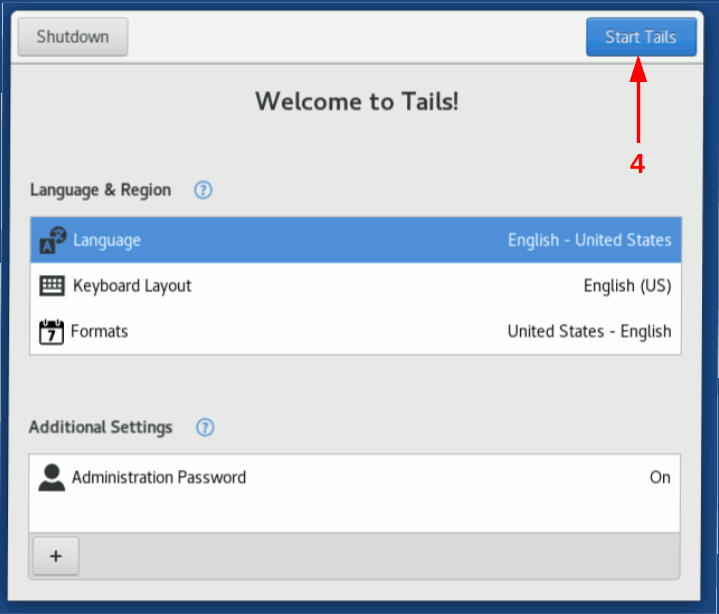
Image 3: Greeting Tails screen
Be sure to copy the shell scripts to an accessible place such as /home/amnesia/mumble-scripts.
In persistence mode, it is recommended to copy the scripts to /home/amnesia/Persistent/mumble-scripts so that they would be accessible after reboot.
Open a console.
Become root using the sudo command.
sudo -iGive execution permissions with the following command:
chmod 755 /home/amnesia/mumble-scripts/*.shTo configure the Mumble server run:
/home/amnesia/mumble-scripts/setup-mumble.shAt the end of the command execution there would be an .onion address shown in the screen, as it can be seen in the red box in the following image. The .onion address is also copied to the clipboard so it could be easier to share.
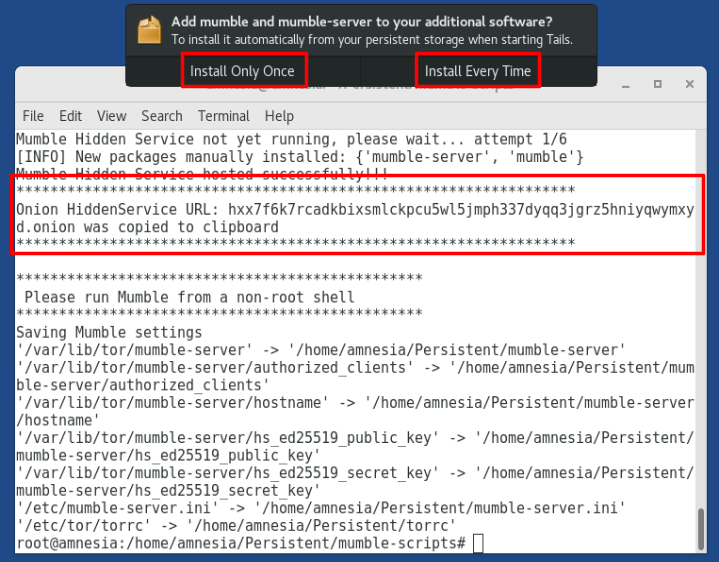
Image 4: Execution of the setup-mumble.sh
It is important to notice that in image 4, the options Install Only Once and Install Every Time would be presented. The first option is useful if Mumble is going to be used only once; the second option is recommended if Mumble will be used on a recurring basis so it would always be accessible.
In the Applications menu, under the Internet section, the Mumble program is accessible as shown in image 5:
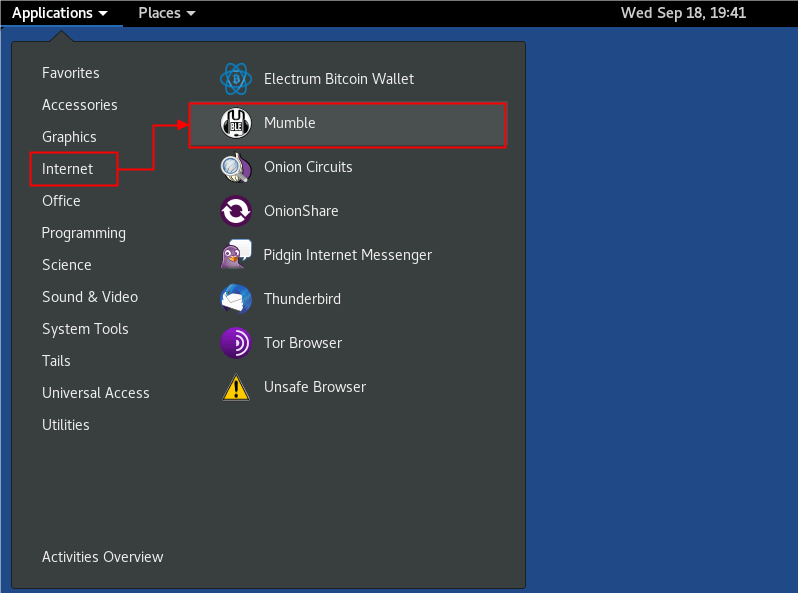
Imagen 5: Mumble execution.
Note: As an alternative, the command mumble can be executed from the command line with an unprivileged user.
Share the .onion address with other conference participants. For this, use the communication tools provided by Tails, such as, encrypted chat, secure mail or others.
Configure Mumble
The first time Mumble is executed, the voice configuration wizard will be launched. If headphones are not used, it is recommended to select “push to talk” option on the “Voice Activity” window as seen in image 6. This way, the microphone will be activated only when the push button is pressed and that will solve most of the echo problems that could happen.
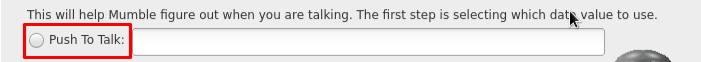
Image 6: Select the push to talk option in Mumble.
Once the wizard has finished, a new connection should be configured. For this, select “add new” and setup the following information as seen in image 7.
Setup the connection configuration as follows:
- Label: Connection name.
- Address: The
.onionaddress. - Port: Leave the default.
- Username: Put an user alias, it can be anything.
In the third step you should click on “connect”. After this, a certificated error message will be presented. This message can be ignored, as authentication with the server is managed by the Hidden Service.
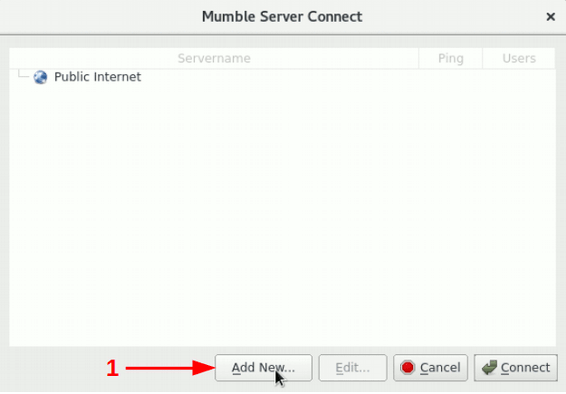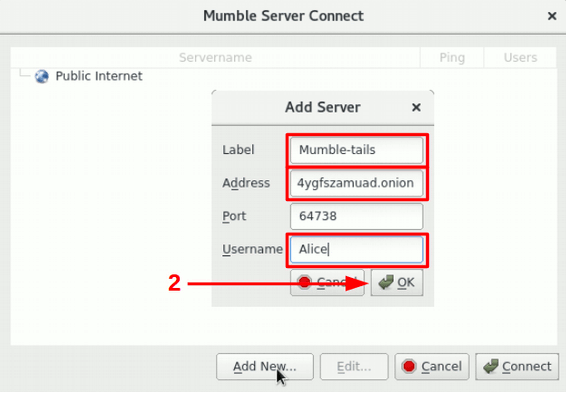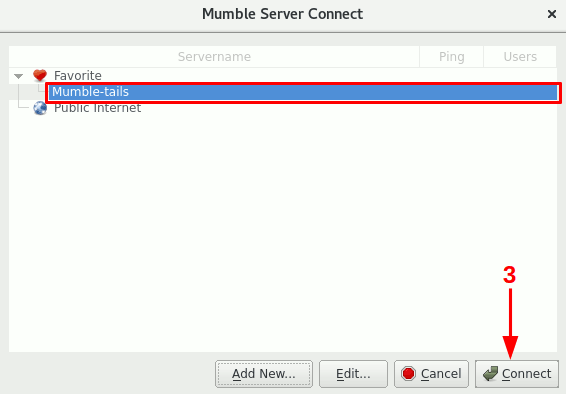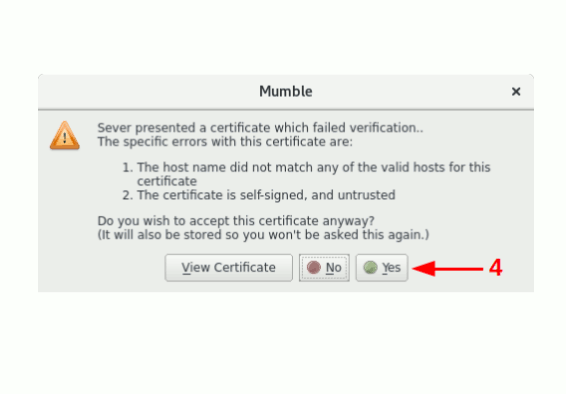
Image 7: Configure Mumble connection.
Once these steps are finished, both Alice and Bob will be able to talk with each other as seen in image 15.
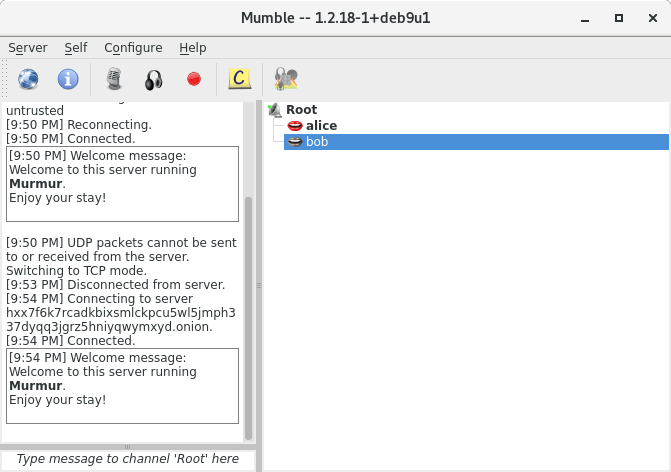
Image 8: Established connection and connected clients.
Conclusions
This solution uses the security, privacy and anonymity features of Tails, and combines them with Mumble to offer acceptable secure communications. If the local Internet provider tries to spy the communication, they could know Alice is using Tor, but not what for. Since there is no VoIP provider, that adversary is eliminated from the thread model.
This is not a perfect solution and there are some considerations that need to be taken into account. The use of Tor could delay the voice communication and this could make the conversations overlap. For this solution to work, it is important that only one person speaks at the same time.
The upload bandwidth should be taken into account because it is a full-duplex connection. This is a very important consideration for the person running the server as she would need to create n communication channels. If Alice is the person hosting the server with 4 people, then she would need to start 4 communication channels.
Basic Linux command line knowledge is necessary because this is not a complete solution, but a proof of concept. To improve the user’s experience, a future version should include a graphic interface as part of a packaged solution.
The Tails operating system offers secure communications for chat and email, but lacks a solution for real time VoIP. The scripts presented here could be used as an input for the Tails project to take into account for future versions.
Source Code
In this section, we share the source code developed for this solution.
setup-mumble.sh
back
#!/bin/bash
TORRC_ROOT=/etc/tor
ETC_ROOT=/etc
HSDIR_ROOT=/var/lib/tor
PERSISTENT_DEVICE=/dev/mapper/TailsData_unlocked
PERSISTENT_ROOT=/home/amnesia/Persistent
# Hidden Service port
HS_PORT=64738
MUMBLE_SERVER_STATUS=-1
TOR_STATUS=-1
ONION_URL='-'
## Validating Tor service status
TOR_STATUS=$(systemctl is-active tor)
echo "Tor service status ${TOR_STATUS}"
if [ "${TOR_STATUS}" == "inactive" ];
then
echo "Starting Tor service"
systemctl start tor
sleep 5
fi
## Install Mumble Client and Server
apt-get update
apt-get install mumble-server mumble -y
## Configure Hidden Service script for Mumble
echo "Backing up original torrc configuration"
cp -pv ${TORRC_ROOT}/torrc ${TORRC_ROOT}/torrc.orig
echo "Configure Hidden Service for Mumble in torrc"
sed -e "/#HiddenServicePort 22 127.0.0.1:22/a \
\\\\n\
# Mumble hidden service configuration.\n\
HiddenServiceDir ${HSDIR_ROOT}/mumble-server/\n\
HiddenServicePort ${HS_PORT} 127.0.0.1:${HS_PORT}" \
< ${TORRC_ROOT}/torrc.orig \
> ${TORRC_ROOT}/torrc
## Configure Mumble Server script to listen only on localhost
echo "Backing up original Mumble Server configuration"
cp -pv ${ETC_ROOT}/mumble-server.ini ${ETC_ROOT}/mumble-server.ini.orig
echo "Configure Mumble Server to bind to localhost"
sed -e "s/#host=/host=localhost/" \
< ${ETC_ROOT}/mumble-server.ini.orig \
> ${ETC_ROOT}/mumble-server.ini
## Validating Mumble server service status
MUMBLE_SERVER_STATUS=$(systemctl is-active mumble-server.service)
echo "Mumble Server status ${MUMBLE_SERVER_STATUS}"
if [ "${MUMBLE_SERVER_STATUS}" == "active" ];
then
echo "Restarting Mumble Server"
systemctl restart mumble-server.service
fi
## Validating Tor service status, make sure it is running.
TOR_STATUS=$(systemctl is-active tor)
echo "Tor service status ${TOR_STATUS}"
if [ "${TOR_STATUS}" == "active" ];
then
echo "Restarting Tor service"
systemctl restart tor
for i in {1..6}
do
if [ -f ${HSDIR_ROOT}/mumble-server/hostname ];
then
echo "Mumble Hidden Service hosted successfully!!!"
break
fi
echo "Mumble Hidden Service not yet running, please wait... attempt ${i}/6"
sleep 5
done
if [ -f ${HSDIR_ROOT}/mumble-server/hostname ];
then
ONION_URL=$(cat ${HSDIR_ROOT}/mumble-server/hostname)
echo ${ONION_URL} | xclip -selection c
echo "******************************************************************"
echo "Onion HiddenService URL: ${ONION_URL} was copied to clipboard"
echo "******************************************************************"
echo
echo "************************************************"
echo " Please run Mumble from a non-root shell"
echo "************************************************"
else
echo "************************************************"
echo "Mumble Hidden Service hosting failed!!!"
echo "Please check the system and try again..."
echo "************************************************"
fi
fi
## Save data for persistent mode.
if [ -e ${PERSISTENT_DEVICE} ]
then
echo "Saving Mumble settings"
cp -avr ${HSDIR_ROOT}/mumble-server ${PERSISTENT_ROOT}
cp -pv ${ETC_ROOT}/mumble-server.ini ${PERSISTENT_ROOT}
cp -pv ${TORRC_ROOT}/torrc ${PERSISTENT_ROOT}
firestore-mumble.sh
back
#!/bin/bash
TORRC_ROOT=/etc/tor
ETC_ROOT=/etc
HSDIR_ROOT=/var/lib/tor
PERSISTENT_ROOT=/home/amnesia/Persistent
ONION_URL='-'
# Move folder and files needes from Persistent location to respective
# OS locations for order to host Mumble hidden service.
cp -avr ${PERSISTENT_ROOT} ${HSDIR_ROOT}
cp -pv ${PERSISTENT_ROOT}/mumble-server.ini ${ETC_ROOT}
cp -pv ${PERSISTENT_ROOT}/torrc ${TORRC_ROOT}
## Restart Tor service to initialize Mumble hidden service
echo "Restarting Tor service"
systemctl restart tor
for i in {1..6}
do
if [ -f ${HSDIR_ROOT}/mumble-server/hostname ];
then
echo "Mumble Hidden Service hosted successfully!!!"
break
fi
echo "Mumble Hidden Service not yet running, please wait... attempt ${i}/6"
sleep 5
done
## Get the Mumble Hidden Service URL and display it to the user
if [ -f ${HSDIR_ROOT}/mumble-server/hostname ];
then
ONION_URL=$(cat ${HSDIR_ROOT}/mumble-server/hostname)
echo ${ONION_URL} | xclip -selection c
echo "******************************************************************"
echo "Onion HiddenService URL: ${ONION_URL} was copied to clipboard"
echo "******************************************************************"
echo
echo "************************************************"
echo " Please run Mumble from a non-root shell"
echo "************************************************"
else
echo "************************************************"
echo "Mumble Hidden Service hosting failed!!!"
echo "Please check the system and try again..."
echo "************************************************"
fipurge-mumble.sh
back
#!/bin/bash
ETC_ROOT=/etc
TORRC_ROOT=/etc/tor
HSDIR_ROOT=/var/lib/tor
PERSISTENT_DEVICE=/dev/mapper/TailsData_unlocked
PERSISTENT_ROOT=/home/amnesia/Persistent
# Starting the purge
echo "Stopping Mumble Server"
systemctl stop mumble-server.service
echo "Purging mumble"
apt purge mumble mumble-server -y
apt autoremove -y
echo "Restoring torrc"
cp -pv ${TORRC_ROOT}/torrc.orig ${TORRC_ROOT}/torrc
echo "Removing Mumble hosting file"
rm -r ${HSDIR_ROOT}/mumble-server
echo "Restarting Tor service"
systemctl restart tor
# Purge data for persistent mode.
if [ -e ${PERSISTENT_DEVICE} ]
then
echo "Purging persistent data for Mumble"
rm -f ${ETC_ROOT}/mumble-server.ini.orig
rm -f ${PERSISTENT_ROOT}/mumble-server.ini
rm -rf ${PERSISTENT_ROOT}/mumble-server
fi